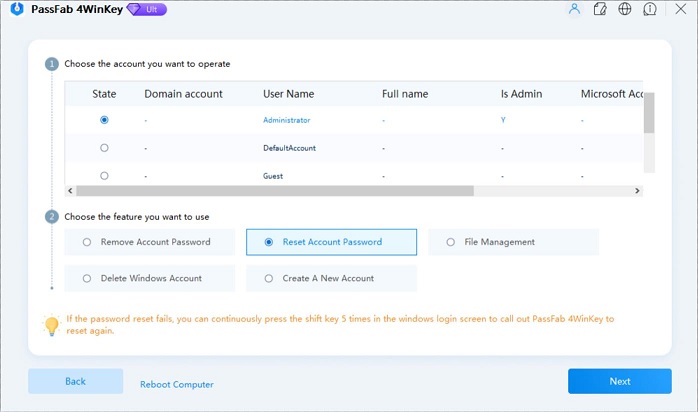
If you forgot your Microsoft account password, you can easily change Windows 8 password online in following step: Visit Microsoft's password reset website on any browser on any computer or device. Type your Microsoft account in the account filed and then the verification code. After Windows 8, people are mostly using their official Microsoft account to log into their Windows. In case you forgot your password in Microsoft account, simply use another unlocked computer to visit the password reset page on Microsoft site and reset the password online. It is a lot easier than resetting the password on local account.
- Windows 8 Microsoft Account Login
- Free Windows 8 Password Reset
- Crack Windows 8 Microsoft Account Password Free
- Windows 8 Microsoft Account Vs Local Account
- Crack Windows 8 Microsoft Account Password Download
- Windows 8 Password Recovery Free
Picture the scene.
You're logged into your PC and have your best friend over for dinner. You guys go way back to grade school and used to play in the same sandbox. Good friends. Buddies for life. Or so you thought…
After downing a few beers you race to the bathroom and your nefarious friend immediately jumps into the drivers seat of your computer.
Since you didn't lock your box he has no problem owning your PC. In minutes he's disabled your AV program, downloaded an exploitation tool from the internet, executed a powershell script and owned all the accounts that ever logged into your computer.
- Your local Administrator account
- Your Microsoft account
- Your wife's account
- Your son's account
- And all the other user accounts that ever used the machine
And since people typically use the same password for everything (According to Sophos, 55% to be exact), your duplicitous 'friend' now has the keys to multiple kingdoms. For example, if he knows your Gmail address he can attempt to sign in using the password culled from your local and Microsoft accounts.
To top it all off, he's doing this on your brand spanking new Windows 8.1 PC which has all the updates installed and is running Windows Defender.
So here's my question: could this really happen?
Yup. And I'm about to walk you through the entire process – step by step. Prepare to be appalled.
For the longest time, I've told you how imperative it is to use a password that is both strong and memorable.
Your password must be strong so that it can't be easily brute forced and memorable so you don't compromise your password by writing it down.
But what's the point of using a convoluted password when a determined hacker can bypass these security methods through unconventional means?
Today I'm going to show you how to hack any Windows PC in less than 5 minutes then I'll share my recommendations for thwarting this threat in the future. Obviously do not try this on someone in real life – this is purely for educational purposes. I trust my readers aren't so vile that they would use this to really compromise a friends PC.
Okay, are you ready?
Let's go. Vonnie is about to leave you aghast.
The problem is that Windows stores encrypted user passwords in memory.
Instead of encrypting a one-way hash the password itself is encrypted and left in memory. This is what happens with the Local Security Authority Subsystem Service (LSASS.exe) process. It's the critical process than manages password changes and authentication.
The fact that the password is encrypted doesn't really mean anything when you realize it's implementation depends on two basic Win32 functions:
- LsaProtectMemory (The encryption function)
- LsaUnprotectMemory (The decryption function)
There's a hole in the implementation that makes it easy for someone to steal the encrypted passwords from memory and use the LsaUnprotectMemory function to decrypt and display the password in plaintext.
The disquieting part is the entire exploit took me less than 5 minutes to pull off.
This is how I did it.
Poaching Passwords
Go to http://blog.gentilkiwi.com/mimikatz and download the latest mimikatz binary. The blog is in French but it's pretty obvious where the binary lives.
Plus, this might be a good opportunity for you to learn a new language. So don't complain – French is the sexiest language on earth so learning this will probably get you a hot wife.
Download, extract and execute the file: mimikatz.exe
Now we need to use PowerShell to dump the contents of memory related to LSASS.exe – but we can't do that because Windows has no default Cmdlet for pulling this off.
Oh what to do?
Import Matthew Graeber'sOut-Minidump.ps1 from Github. Peruse the code by clicking the link so you get a basic understanding about what it does.
The first thing you should do is analyze the PS1 file in detail. The file is littered with comments to make it easier to understand.
I just want you to see why this works rather then just telling you how it works.
Read and proceed.
After you get an idea about what happening, right click the link, choose Save link as from the context menu and make sure you save it with the PS1 File (.ps1) file extension. It won't work if you save it as a .txt file.
Okay, now we need to import the script into Powershell so we can do our memory dump dance.
Open PowerShell as an Administrator by pressing the Windows Logo Key + q and typing:
powershell
Windows 8 Microsoft Account Login
Since PowerShell scripts can completely nuke your system, Windows sagaciously disables such scripts by default.
To change this, we need to temporarily set the Execution Policy to Unrestricted. By the way, after running the script you should change the execution policy back to Restricted.
Type:
Set-ExecutionPolicy Unrestricted
Then import the script by typing a dot followed by the path to your PS1.
. C:UsersvhudsonDocumentsScriptsPowerShellOut-Minidump.ps1
In geek speak this is known as 'Dot Sourcing' the script and it's one way to import functions into PowerShell.
Free Windows 8 Password Reset
You'll see a fusillade of security warnings – which is good. But that's why I told you to examine the script first. Never wantonly execute a scripts that you find online. Always investigate the code first so you can have some idea what it does.
Press 'r' to run the script and then perform the memory dump:
Get-Process lsass | Out-Minidump
The dump is hanging out in %WINDIR%System32 but we need to move it to a different location so we can view it. Use the Copy-Item Cmdlet to do that.
Copy-Item .lsass_516.dmp C:UsersVonnieDocumentsScriptsPowerShell
Great now we're ready to rock.
Flip back over to the mimikatz terminal and load in the LSASS dump we captured in PowerShell.
sekurlsa::minidump C:UsersVonnieDocumentsScriptsPowerShelllsass_516.dmp
It should switch to the MINIDUMP file so now we can view the passwords
Now punch in:
sekurlsa::logonPasswords full
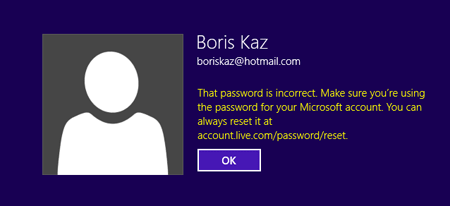
Ladies and Gentlemen what you have before your eyes is my actual Microsoft account password. (the username is just two lines up).
In plaintext.
Vulnerable and exposed.
This means someone with this account now has unfettered access to:
- My Skype account
- Outlook.com emails
- Office 365 Subscription
- The Windows Store (they can make purchases)
- All my files, photos, and music sitting in OneDrive
- My XBox Live account
- All my Windows 8.1 desktop and computer settings
- My freggin' life
If I had other accounts on the system you would see them as well by simply scrolling down.
Do you see how easy it is to p0wn someone? Don't let this happen to you. Here's how to protect yourself.
Protect yo' self before you wreck yo' self.
There are a few things you can do to prevent this kind of the thing.
The easiest is to simply lock your box when you leave your computer. Get into the habit of pressing the Windows Logo Key + l (that's a lower case 'L') to lock your computer.
You can also configure your screensaver to display a password prompt on resume. Just right click the Desktop, choose Personalize and in the Screen Saver section put a check mark in On resume display logon screen.
You can also thwart the threat by deleting the wdigest line from the SecurityPackages key in
Finally, leaving your antivirus software running would have slowed down the attacker. Of course, if your box is unlocked there's nothing stopping your assailant from disabling Windows Defender and working around your little registry hack. That's why you should always lock your box.
Repeat after me:
- Windows Key + L!
- Windows Key + L!
- Windows Key + L!
The Bottom Line
Lock your box. Period.
Sensible computer users will always advise you that protecting your user account on your Windows installation with a password is a very important thing to do. And of course, that is correct to help protect and secure private and important data from other users that have access to the same machine. It isn't the case anymore though that simply putting a password on your account will protect you and your files if someone is desperate enough to want to get in.
There are of course legitimate reasons for wanting to get around a user account password. I've lost count the number of times someone has left me with a PC to work on and gone off not telling me what the password is. Some users are so forgetful, they can't even remember what their own password is, and you'd be surprised how many people actually do that. It's not a major surprise really when there are possibly 10+ different passwords to remember while using your PC and online etc.
We've posted quite a few articles on how to get into Windows without knowing any user's account password. There's the wonderful password bypass tool Kon-Boot, and a number of password resetting tools like PCLoginNow or Offline Windows Password Editor. Then there's the hack to get into XP without changing the password. Here's another method which allows you to crack the Windows user account password and get into Windows which means leaving the current password intact and not resetting it.Ophcrack is a Windows password cracker that works on the principle of using an advanced text based table of words (rainbow table) to try and discover the password. Although Ophcrack actually has several different tables which can increase the effectiveness of discovering the password, all but the free basic ones are commercial tables that cost at least $99 each. Therefore there are a few limitations on the free version in regards to what type of passwords it can recover.
The Ophcrack program is available in either a Windows (or Linux) installer or a downloadable Linux based LiveCD ISO which you can simply burn to CD and boot from it. There are separate Windows XP and Vista/7 ISO's and they are not interchangeable because of the way the different versions of Windows store their login passwords. XP uses LM hashes for its passwords, Vista and 7 use NT Hashes which are much more secure and as a consequence much harder to crack. The 2 o/s specific ISO images on the website already contain the free rainbow tables and are ready to go.
We'll simply concentrate on the LiveCD version here as it's the most useful and doesn't need access to the system through another account. Using Ophcrack is actually really very simple and the majority of users have to press a maximum of 1 or 2 keys to get a result. All you need to know is how to burn an ISO to a CD and then boot from it.
When you boot the CD there will be a selection screen where you can choose the graphics mode. If automatic doesn't work then try text mode, or the low RAM option for older machines. Once the Linux system has booted the ophcrack program will automatically start trying to crack the passwords. After some time, depending on the speed of the system, the account will either show the password or a 'not found' in red if ophcrack failed to discover the password.
For multi boot systems or where the program has failed to detect your accounts, a SAM registry file containing the passwords can be loaded manually by clicking on Load -> Encrypted SAM, go to Computer/Media and the hard drives will be listed as hda1, hda2 etc. Go into the required hard drive and navigate to the Windows/System32/Config folder and click Choose. The accounts should now appear and you can press Crack to begin the process.
This type of password cracking is heavily dependent on what sort of password the program is trying to crack with the free version of the rainbow tables and also which o/s the account is in. For example, in XP you can crack 14 alphanumeric characters with a mixture of numbers, upper and lower case letters. The Vista/7 limit is 16 characters and the tables are dictionary based meaning the words from the password have to be in the dictionary. None of the free tables are able to recognize special characters such as spaces, full stops, commas etc.
As a simple test, raymondcc as a password is found in both versions, but raYmondcc is not found in the Vista/7 table because of the upper case 'Y' in the middle. raymondccblog is also not found in vista/7, but that and something like raYmondCCbloG is found in the XP version. In short, the Vista and 7 cracking will only get out common names and words which don't have numbers or case differences inserted at random, whereas the XP cracking can handle far more combinations.
Download Ophcrack
You might also like:
Setting Windows User Account with Random PasswordReset Windows User Account by Removing Forgotten Password5 Ways to Change Windows User Password Without Knowing Current PasswordRecover Windows Login Password Online with LoginRecovery3 Ways to Change a Windows User Account Into an Administratorthe live cd works fast on xp, etc I used many times, but on HP elitebook 820 I never succeeded to manage the boot maybe due to UEFI files? can you please advise,
I also tried to run in on other HP (pc) win 7 and everything went ok
Can Ophcrack be detected by anti-virus? And once the program runs and your computer shuts off, when you reboot is there any trace of the Ophcrack program?
ReplyIf you use the BootCD, there are no traces of the program left on your computer because it doesn't install anything.
Using the setup installer, it leaves nothing behind when you uninstall the program and tables with the official uninstaller.
As for antivirus software, some of them will flag the program as 'legitimate software that can be used to harm your computer or steal data', or something similar.
Since you didn't lock your box he has no problem owning your PC. In minutes he's disabled your AV program, downloaded an exploitation tool from the internet, executed a powershell script and owned all the accounts that ever logged into your computer.
- Your local Administrator account
- Your Microsoft account
- Your wife's account
- Your son's account
- And all the other user accounts that ever used the machine
And since people typically use the same password for everything (According to Sophos, 55% to be exact), your duplicitous 'friend' now has the keys to multiple kingdoms. For example, if he knows your Gmail address he can attempt to sign in using the password culled from your local and Microsoft accounts.
To top it all off, he's doing this on your brand spanking new Windows 8.1 PC which has all the updates installed and is running Windows Defender.
So here's my question: could this really happen?
Yup. And I'm about to walk you through the entire process – step by step. Prepare to be appalled.
For the longest time, I've told you how imperative it is to use a password that is both strong and memorable.
Your password must be strong so that it can't be easily brute forced and memorable so you don't compromise your password by writing it down.
But what's the point of using a convoluted password when a determined hacker can bypass these security methods through unconventional means?
Today I'm going to show you how to hack any Windows PC in less than 5 minutes then I'll share my recommendations for thwarting this threat in the future. Obviously do not try this on someone in real life – this is purely for educational purposes. I trust my readers aren't so vile that they would use this to really compromise a friends PC.
Okay, are you ready?
Let's go. Vonnie is about to leave you aghast.
The problem is that Windows stores encrypted user passwords in memory.
Instead of encrypting a one-way hash the password itself is encrypted and left in memory. This is what happens with the Local Security Authority Subsystem Service (LSASS.exe) process. It's the critical process than manages password changes and authentication.
The fact that the password is encrypted doesn't really mean anything when you realize it's implementation depends on two basic Win32 functions:
- LsaProtectMemory (The encryption function)
- LsaUnprotectMemory (The decryption function)
There's a hole in the implementation that makes it easy for someone to steal the encrypted passwords from memory and use the LsaUnprotectMemory function to decrypt and display the password in plaintext.
The disquieting part is the entire exploit took me less than 5 minutes to pull off.
This is how I did it.
Poaching Passwords
Go to http://blog.gentilkiwi.com/mimikatz and download the latest mimikatz binary. The blog is in French but it's pretty obvious where the binary lives.
Plus, this might be a good opportunity for you to learn a new language. So don't complain – French is the sexiest language on earth so learning this will probably get you a hot wife.
Download, extract and execute the file: mimikatz.exe
Now we need to use PowerShell to dump the contents of memory related to LSASS.exe – but we can't do that because Windows has no default Cmdlet for pulling this off.
Oh what to do?
Import Matthew Graeber'sOut-Minidump.ps1 from Github. Peruse the code by clicking the link so you get a basic understanding about what it does.
The first thing you should do is analyze the PS1 file in detail. The file is littered with comments to make it easier to understand.
I just want you to see why this works rather then just telling you how it works.
Read and proceed.
After you get an idea about what happening, right click the link, choose Save link as from the context menu and make sure you save it with the PS1 File (.ps1) file extension. It won't work if you save it as a .txt file.
Okay, now we need to import the script into Powershell so we can do our memory dump dance.
Open PowerShell as an Administrator by pressing the Windows Logo Key + q and typing:
powershell
Windows 8 Microsoft Account Login
Since PowerShell scripts can completely nuke your system, Windows sagaciously disables such scripts by default.
To change this, we need to temporarily set the Execution Policy to Unrestricted. By the way, after running the script you should change the execution policy back to Restricted.
Type:
Set-ExecutionPolicy Unrestricted
Then import the script by typing a dot followed by the path to your PS1.
. C:UsersvhudsonDocumentsScriptsPowerShellOut-Minidump.ps1
In geek speak this is known as 'Dot Sourcing' the script and it's one way to import functions into PowerShell.
Free Windows 8 Password Reset
You'll see a fusillade of security warnings – which is good. But that's why I told you to examine the script first. Never wantonly execute a scripts that you find online. Always investigate the code first so you can have some idea what it does.
Press 'r' to run the script and then perform the memory dump:
Get-Process lsass | Out-Minidump
The dump is hanging out in %WINDIR%System32 but we need to move it to a different location so we can view it. Use the Copy-Item Cmdlet to do that.
Copy-Item .lsass_516.dmp C:UsersVonnieDocumentsScriptsPowerShell
Great now we're ready to rock.
Flip back over to the mimikatz terminal and load in the LSASS dump we captured in PowerShell.
sekurlsa::minidump C:UsersVonnieDocumentsScriptsPowerShelllsass_516.dmp
It should switch to the MINIDUMP file so now we can view the passwords
Now punch in:
sekurlsa::logonPasswords full
Ladies and Gentlemen what you have before your eyes is my actual Microsoft account password. (the username is just two lines up).
In plaintext.
Vulnerable and exposed.
This means someone with this account now has unfettered access to:
- My Skype account
- Outlook.com emails
- Office 365 Subscription
- The Windows Store (they can make purchases)
- All my files, photos, and music sitting in OneDrive
- My XBox Live account
- All my Windows 8.1 desktop and computer settings
- My freggin' life
If I had other accounts on the system you would see them as well by simply scrolling down.
Do you see how easy it is to p0wn someone? Don't let this happen to you. Here's how to protect yourself.
Protect yo' self before you wreck yo' self.
There are a few things you can do to prevent this kind of the thing.
The easiest is to simply lock your box when you leave your computer. Get into the habit of pressing the Windows Logo Key + l (that's a lower case 'L') to lock your computer.
You can also configure your screensaver to display a password prompt on resume. Just right click the Desktop, choose Personalize and in the Screen Saver section put a check mark in On resume display logon screen.
You can also thwart the threat by deleting the wdigest line from the SecurityPackages key in
Finally, leaving your antivirus software running would have slowed down the attacker. Of course, if your box is unlocked there's nothing stopping your assailant from disabling Windows Defender and working around your little registry hack. That's why you should always lock your box.
Repeat after me:
- Windows Key + L!
- Windows Key + L!
- Windows Key + L!
The Bottom Line
Lock your box. Period.
Sensible computer users will always advise you that protecting your user account on your Windows installation with a password is a very important thing to do. And of course, that is correct to help protect and secure private and important data from other users that have access to the same machine. It isn't the case anymore though that simply putting a password on your account will protect you and your files if someone is desperate enough to want to get in.
There are of course legitimate reasons for wanting to get around a user account password. I've lost count the number of times someone has left me with a PC to work on and gone off not telling me what the password is. Some users are so forgetful, they can't even remember what their own password is, and you'd be surprised how many people actually do that. It's not a major surprise really when there are possibly 10+ different passwords to remember while using your PC and online etc.
We've posted quite a few articles on how to get into Windows without knowing any user's account password. There's the wonderful password bypass tool Kon-Boot, and a number of password resetting tools like PCLoginNow or Offline Windows Password Editor. Then there's the hack to get into XP without changing the password. Here's another method which allows you to crack the Windows user account password and get into Windows which means leaving the current password intact and not resetting it.Ophcrack is a Windows password cracker that works on the principle of using an advanced text based table of words (rainbow table) to try and discover the password. Although Ophcrack actually has several different tables which can increase the effectiveness of discovering the password, all but the free basic ones are commercial tables that cost at least $99 each. Therefore there are a few limitations on the free version in regards to what type of passwords it can recover.
The Ophcrack program is available in either a Windows (or Linux) installer or a downloadable Linux based LiveCD ISO which you can simply burn to CD and boot from it. There are separate Windows XP and Vista/7 ISO's and they are not interchangeable because of the way the different versions of Windows store their login passwords. XP uses LM hashes for its passwords, Vista and 7 use NT Hashes which are much more secure and as a consequence much harder to crack. The 2 o/s specific ISO images on the website already contain the free rainbow tables and are ready to go.
We'll simply concentrate on the LiveCD version here as it's the most useful and doesn't need access to the system through another account. Using Ophcrack is actually really very simple and the majority of users have to press a maximum of 1 or 2 keys to get a result. All you need to know is how to burn an ISO to a CD and then boot from it.
When you boot the CD there will be a selection screen where you can choose the graphics mode. If automatic doesn't work then try text mode, or the low RAM option for older machines. Once the Linux system has booted the ophcrack program will automatically start trying to crack the passwords. After some time, depending on the speed of the system, the account will either show the password or a 'not found' in red if ophcrack failed to discover the password.
For multi boot systems or where the program has failed to detect your accounts, a SAM registry file containing the passwords can be loaded manually by clicking on Load -> Encrypted SAM, go to Computer/Media and the hard drives will be listed as hda1, hda2 etc. Go into the required hard drive and navigate to the Windows/System32/Config folder and click Choose. The accounts should now appear and you can press Crack to begin the process.
This type of password cracking is heavily dependent on what sort of password the program is trying to crack with the free version of the rainbow tables and also which o/s the account is in. For example, in XP you can crack 14 alphanumeric characters with a mixture of numbers, upper and lower case letters. The Vista/7 limit is 16 characters and the tables are dictionary based meaning the words from the password have to be in the dictionary. None of the free tables are able to recognize special characters such as spaces, full stops, commas etc.
As a simple test, raymondcc as a password is found in both versions, but raYmondcc is not found in the Vista/7 table because of the upper case 'Y' in the middle. raymondccblog is also not found in vista/7, but that and something like raYmondCCbloG is found in the XP version. In short, the Vista and 7 cracking will only get out common names and words which don't have numbers or case differences inserted at random, whereas the XP cracking can handle far more combinations.
Download Ophcrack
You might also like:
Setting Windows User Account with Random PasswordReset Windows User Account by Removing Forgotten Password5 Ways to Change Windows User Password Without Knowing Current PasswordRecover Windows Login Password Online with LoginRecovery3 Ways to Change a Windows User Account Into an Administratorthe live cd works fast on xp, etc I used many times, but on HP elitebook 820 I never succeeded to manage the boot maybe due to UEFI files? can you please advise,
I also tried to run in on other HP (pc) win 7 and everything went ok
Can Ophcrack be detected by anti-virus? And once the program runs and your computer shuts off, when you reboot is there any trace of the Ophcrack program?
ReplyIf you use the BootCD, there are no traces of the program left on your computer because it doesn't install anything.
Using the setup installer, it leaves nothing behind when you uninstall the program and tables with the official uninstaller.
As for antivirus software, some of them will flag the program as 'legitimate software that can be used to harm your computer or steal data', or something similar.
ReplyVery helpful. Thank you very much
Replythankss… it worked for me….. hurrayyyyyyyy…..
Replyophcrack is an exellent program 4 cracking passwords. it worked first time when i used it and it hasnt failed yet.
Crack Windows 8 Microsoft Account Password Free
ReplyThanks for this great programs i just make the cdlive and boot and rescue a computer password i was going to reset it but with this program it take me 1 hour to find the password and make it work again !! great work!
thanks a lot!
gotic.
thanks :)
Windows 8 Microsoft Account Vs Local Account
ReplyGuys, just to share my experience with this cd:)
passwords up to 14 characters (letters and digits) are cracked within minutes:) But, if you have a longer password and use special characters in your password, forget about it:)
No way
ya peeps this does works it just the chance of read it and click the right buttons ! yes it worked first time for me so thanks! i was really get sick of the old version! cheers!
Replyworked like a champ,
Crack Windows 8 Microsoft Account Password Download
good stuff i just subscribed to your blog
Reply
